
What are the risks of Operational Technology?
We are living in the era of digital transformation and most companies now rely heavily on technology. Operational technology enables companies to enhance their efficiency and productivity.
OT provides organizations with the ability to better automate, control, and monitor these processes and ultimately integrate them with operational and financial management systems. Supervisory Control and Data Acquisition (SCADA) is an example that businesses use OT for.
Information technology and operational technology can be combined to maximize work. But the convergence of IT and OT has risks. Companies must be aware of these risks to prevent any disruptions from their work and a loss in revenue.
Risks of OT and IT Convergence

The image above illustrates the convergence of OT and IT. You can see that when they are combined it is easier to be targeted by cyber-attacks because there are separate attack surfaces.
A further example of the risks would be the use of cloud platforms, on-premise sites, or both when operating a business. These categories all use OT and IT increasing the attack surface.
An on-premise site uses OT and a Programmable Logic Controller (PLC). However, there are PLCs that are software-based currently being developed, which can sit virtually on a cloud platform. You will also find Human Machine Interfaces (HMI), Manufacturing Execution Systems (MES), and Enterprise Resource Planning (ERP) on an on-premise site.
For a cloud-based site to operate there needs to be HMI, SCADA, MES, and ERP.
Cloud-based platforms offer accessibility, ease of remote management, operating expenses, and redundancy. Small to medium-sized businesses have started to use cloud computing to operate as it helps store files, backup data, disaster recovery, increase collaboration, and test new projects.
An environment that uses a single site, a multi-site, and centralized plus multi-site also uses OT and IT to operate. In a single site, both OT and IT are used in a single environment only and a single network. On multiple sites (federated) also known as an independent, OT and IT will be focused on a single site regardless if it is on-site or on-premise. However, when there are multiple and centralized sites the IT and OT are deployed on multiple sites but managed by a central site.
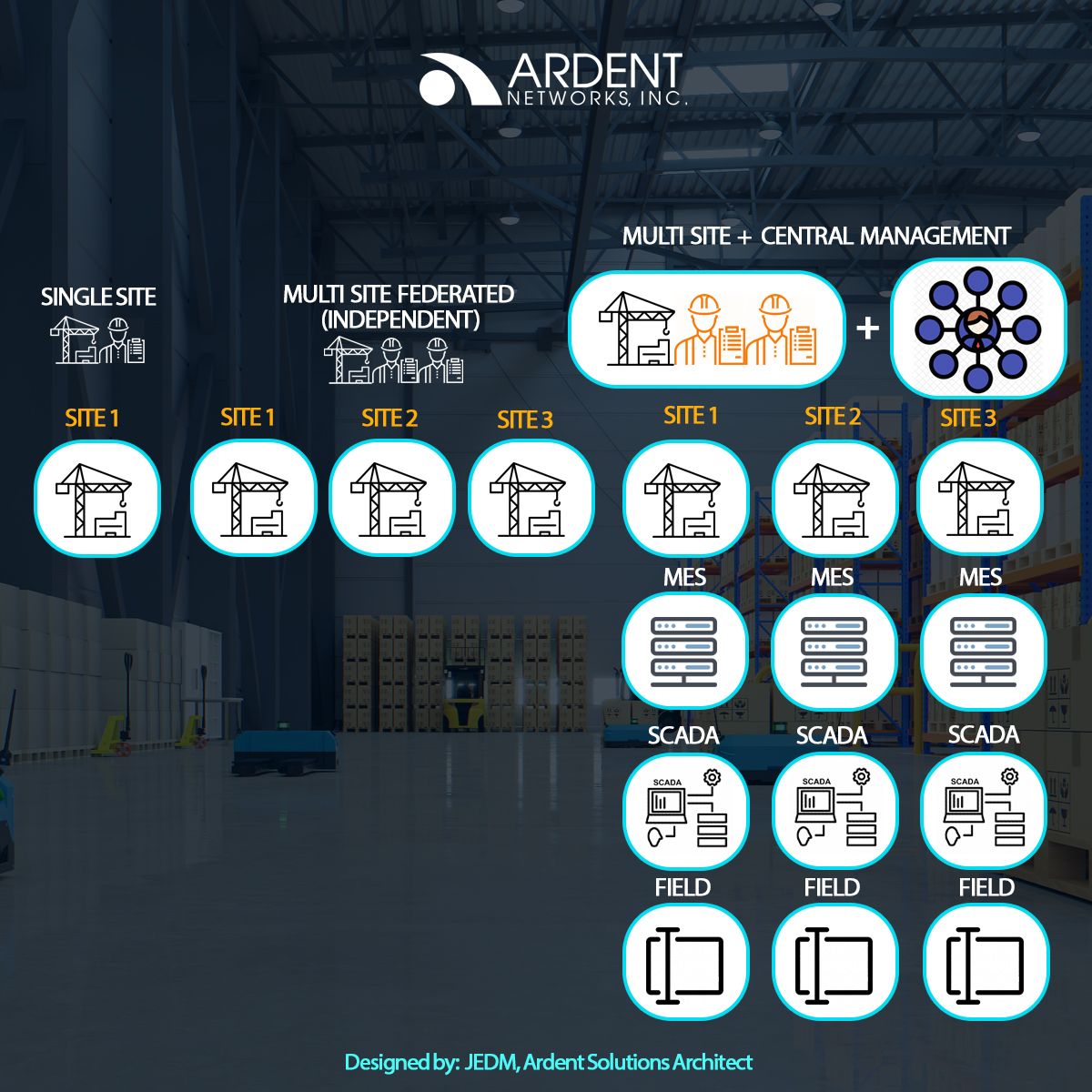
As you can see in the image a central site is on one network and is managed by one management. Each site has an EP, MES, SCADA, HMI, and field level to operate.
Threats that we should look out for
OT Cyber Threats – Before 2020 OT systems were not considered by most companies. However, the appearance of Stuxnet changed this. Stuxnet destroyed 1000 nuclear centrifuges in the Natanz bas (Iran). In this attack, people learned the difference between OT and IT threats. Forensics discovered that the attackers were able to modify the controller while the system was continuously monitored. This shows that the insecure OT space has become an attack territory for cyber-criminals.
Cyber-threat detection – “air-gap” is said to isolate IT and OT systems however Stuxnet showed that even with an “air-gap” the cyber-threat surface is not eliminated. Cyber-threat detection needs to have visibility, but most utilities have limited views on the architecture and services running on their OT systems.
Industrial Control Systems (ICS) – HMI connects human operators to industrial control systems, which are networked to infrastructures. Having access to HMIs from internet-facing businesses is a risk to ICS. It makes HMIs a target to IP-based vulnerabilities like authentication bypass, weak session management, unsecured ICS communication protocoling, and insufficient control traffic encryption.
The Internet of Things (IoT) Explosion – Research shows organizations have IoT technologies connected to their ICS networks. These devices are usually unmanaged, come from a multitude of vendors, use non-standard operating systems, support a diversity of often insecure protocols, and may be connected to other devices inside or outside the companies’ network. IoT devices pave way for various entry points making it easier for cyber attackers to enter your network.
Securing your IT/OT converged environment
OT and IT can work well together reducing costs and improving your revenue. There may be times when OT environments are not managed properly. When using OT, the IT aspects are not covered, which can be done by individuals. This includes audit, risk, IT security, change management, and third-party risk management.
The absence of IT individuals can cause major problems as there is no one there to monitor or solve issues right away. When problems occur for OT, they may not be programmed to fix things in real-time. There is still a need to find a specialist to fix things faster otherwise OT systems can fail and cause delays.
As a company, you need to have an assessment of your OT systems to determine what needs special attention. You need to understand thoroughly that OT still needs to be monitored regularly to ensure that there will be fewer to no problems.
The assessment of OT systems include how well your systems are equipped, engagement of IT, and vendors. You should not solely rely on your vendors as they use laptops or USB devices, which can have a high risk of cyber attacks affecting everyone.
Ardent Networks Inc. is a value-added distributor that provides solutions to help improve productivity for businesses. We are partnered with Fortinet, a leading cybersecurity solutions provider. Their solutions can integrate with your IT/OT converged environment and provide best-of-breed threat protection securing your network and maintain a strong security posture.
If you are interested or have any questions, you may get in touch with us at our Contact Us page on our website: https://ardentnetworks.com.ph/contact-us-2/